The increasing menace of Zero Day Attacks underscores a pivotal concern in the digital world we are living in.
As software becomes more integral to our daily lives, the opportunity for attackers to exploit unseen flaws grows. This escalation not only puts individual users at risk but also jeopardizes the security of corporations and governments.
The aftermath of such attacks can range from financial losses to significant breaches of sensitive information. Thus, understanding Zero Day Attacks is not just a matter for technical experts—it’s a crucial piece of knowledge for anyone navigating the digital world.
In this blog we will explore the intricacies of Zero Day Attacks, their origins, mechanisms, and, most importantly, how we can shield ourselves from these invisible threats.
Also read: Cyber attack: Exploring the consequences of data privacy breaches
- Key Learning Outcome of This Blog
- What is Zero-Day Attack?
- What is a Software Vulnerability?
- Who Are Responsible for Conducting Zero Day Attacks?
- Who are the Primary Targets of Zero Day Attacks?
- The Anatomy of a Zero-Day Attack
- Examples of Zero Day Attacks
- How to Detect Zero Day Attacks?
- How to Protect Your Entity from Zero Day Attacks?
Key Learning Outcome of This Blog
- Unknown Vulnerabilities: Zero Day Attacks target the blind spots in software security, which are unknown flaws or bugs that hackers discover before the developers do. This exploitation means that traditional security measures may not be effective until after the attack has occurred.
- Importance of Software Updates: Regularly updating software is a key defense mechanism against Zero Day Attacks. Software developers release patches and updates to fix vulnerabilities once they’re discovered. Staying updated means closing the windows of opportunity for hackers to exploit these vulnerabilities.
What is Zero-Day Attack?
A Zero-Day Attack refers to a cyber attack that occurs on the same day a vulnerability is discovered in software, before the software developers have had the opportunity to create a patch to fix the vulnerability. This type of attack is particularly dangerous because it exploits a weakness that is unknown to the software vendor at the time of the attack, making it difficult to defend against.
Attackers can use zero-day vulnerabilities to launch malware, ransomware, or other malicious activities, targeting anything from individual users to large organizations.

The term “Zero Day” originates from the world of software piracy, where it referred to the speed at which hackers could crack newly released software. However, its meaning evolved to emphasize the critical window between the discovery of a vulnerability and its patching, highlighting the urgency and risk associated with these vulnerabilities.
You will be surprised to know these Cybersecurity Compliance Standards for Businesses.
Distinction Between Zero Day Vulnerabilities, Exploits, and Attacks
Understanding the distinctions between these terms is crucial for grasping the full scope of the threat posed by Zero Day Attacks.
- Zero Day Vulnerabilities are security flaws that are not known to the software vendor or the security community at large. These vulnerabilities are the initial weakness that could be exploited.
- Zero Day Exploits describe the actual method or code that takes advantage of a Zero Day vulnerability. This exploit is what attackers use to gain unauthorized access or cause damage.
- Zero Day Attacks occur when attackers use a Zero Day exploit to take advantage of a vulnerability, resulting in unauthorized actions that can lead to data theft, system compromise, or other forms of cyber mischief.
Discover the World’s Top Cybersecurity Companies, they are your digital security dream team.
What is a Software Vulnerability?
At the core of every Zero Day Attack lies a software vulnerability—an Achilles’ heel within the software’s code that opens the door to potential exploits by cybercriminals. But what exactly is a software vulnerability? In simple terms, it’s a flaw or weakness in a software system that can be exploited by a threat actor, such as a hacker, to perform unauthorized actions within a computer system.
These vulnerabilities can arise from a variety of sources, including:
- Coding Errors: Mistakes made during the development process can create vulnerabilities. These errors may occur because of oversight, lack of awareness of security best practices, or the complexity of the software.
- Design Flaws: Sometimes, the very architecture of a software system can contain inherent weaknesses that pose security risks. These are not always obvious until explored with a malicious perspective.
- Inadequate Security Updates: Failing to apply updates or patches to software can leave known vulnerabilities exposed to exploitation, making it crucial for users and administrators to stay current with their software’s latest versions.
Understanding software vulnerabilities is essential because they are the entry points that attackers use to initiate Zero Day Attacks. You must see these Key Questions to Prioritize Privacy in Vendor Risk Management.
Who Are Responsible for Conducting Zero Day Attacks?
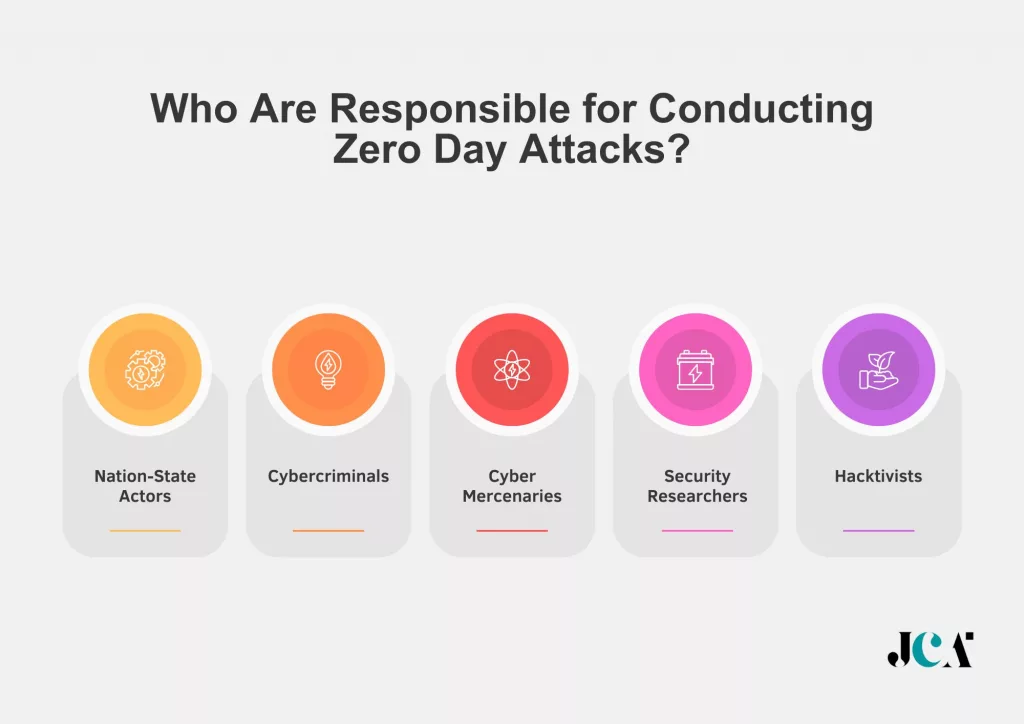
Zero Day Attacks are not random acts of digital vandalism but calculated, sophisticated strikes aimed at exploiting the unknown vulnerabilities of systems for various purposes. The entities behind these attacks often possess advanced technical skills and resources, making them formidable adversaries. Here’s a closer look at who typically carries out Zero Day Attacks:
- Nation-State Actors: Governments around the world have been implicated in Zero Day Attacks, using them as digital weapons for espionage, sabotage, or to gain a strategic advantage over other nations. These actors are well-funded and have access to a vast array of technical resources, making their attacks highly sophisticated and targeted.
- Cybercriminals: Motivated by financial gain, cybercriminal groups exploit Zero Day Vulnerabilities to steal personal information, intellectual property, or direct financial assets. These entities operate in the shadows of the internet, selling stolen data or access to compromised systems on the dark web.
- Hacktivists: Some Zero Day Attacks are carried out by hacktivist groups who are motivated by political or social causes. These groups use their attacks as a form of protest, targeting governments, corporations, or other organizations they view as opponents to their cause.
- Cyber Mercenaries: These are hackers for hire who will exploit Zero Day Vulnerabilities for anyone willing to pay. Their clients may range from private companies engaging in corporate espionage to individuals seeking revenge.
- Security Researchers: In rare cases, security researchers might utilize Zero Day Exploits to demonstrate the vulnerabilities in systems. However, ethical researchers typically report their findings to the affected company to allow for the vulnerability to be patched before it becomes widely known.
Read our trending blog on 7 Tips to Protect Your Business from Cyber Threats.
Who are the Primary Targets of Zero Day Attacks?
Certain sectors and organizations are more attractive targets due to their strategic, financial, or political value. Here’s a breakdown of common targets for Zero Day Exploits:
- Government Agencies: National and local government systems are prime targets due to the sensitive personal and security information they hold, making them attractive for espionage or sabotage purposes, especially by nation-state actors.
- Financial Institutions: Banks, investment firms, and other financial services hold vast amounts of financial data and assets, drawing the attention of cybercriminals looking to make a financial gain through theft or fraud.
- Technology Companies: Given their wealth of intellectual property, customer data, and involvement in critical infrastructure, tech companies are often targeted for corporate espionage or to gain a competitive advantage.
- Healthcare Providers: With access to personal health information, healthcare providers are targeted for the valuable data they hold, which can be sold or used for identity theft.
- Energy Sector: Critical infrastructure, such as power grids and nuclear facilities, are targeted for sabotage, potentially by nation-state actors or terrorist groups seeking to cause widespread disruption.
- Educational Institutions: Universities and research institutions, with their rich repositories of research data and personal information of students and staff, are targets for both espionage and data theft.
- Media and Entertainment: Media organizations can be targeted for censorship, to control or influence public opinion, or for intellectual property theft.
Must read: The Human Factor: Training and Culture in Cybersecurity.
The Anatomy of a Zero-Day Attack
Let’s explore each stage in more detail to comprehend the meticulous planning and execution behind these covert cyber threats.
1. Discovery of Vulnerability:
- Target Identification: Cybercriminals often focus on high-profile targets, including widely used operating systems, popular software applications, or even specific industries. The goal is to maximize the impact of the Zero-Day Attack by exploiting vulnerabilities present in systems widely adopted by individuals or organizations.
- Exploitable Weaknesses: Vulnerabilities can arise from a variety of sources, such as programming errors, flaws in the software design, or unintended consequences of feature implementation. Cyber attackers meticulously analyze code, conduct reverse engineering, and employ automated tools to identify exploitable weaknesses.
2. Crafting the Exploit:
- Zero-Day Exploit Development: Skilled hackers use their expertise to develop a Zero-Day exploit tailored to the specific vulnerability discovered. This process involves creating a set of instructions or code that capitalizes on the weakness, allowing unauthorized access, privilege escalation, or other malicious actions.
- Obfuscation Techniques: To avoid detection by security measures, attackers employ obfuscation techniques to conceal the exploit within seemingly innocuous code. This makes it challenging for traditional antivirus software or intrusion detection systems to identify and mitigate the threat.
3. Launch and Infiltration:
- Delivery Mechanisms: Zero-day exploits are delivered to target systems through various means, such as malicious email attachments, compromised websites, or even network vulnerabilities. Social engineering tactics may be employed to lure users into unknowingly activating the exploit.
- Execution of Malicious Code: Once the exploit is delivered, it triggers the execution of malicious code on the target system. The code may aim to establish a persistent presence, exfiltrate sensitive data, or perform other actions depending on the objectives of the attackers.
- Evasion Techniques: Sophisticated Zero-Day Attacks often incorporate evasion techniques to bypass security measures, such as anti-virus programs, firewalls, and intrusion detection systems. These techniques may involve polymorphic code, which dynamically changes its appearance, making it more challenging for security tools to recognize the malicious behavior.
Roles in Discovering and Exploiting Vulnerabilities
- White Hat Hackers: Ethical hackers who discover vulnerabilities to report them to the software developers for patching, thereby improving security.
- Grey Hat Hackers: Individuals who may discover and exploit vulnerabilities without malicious intent but without the explicit permission of the software owner. Their actions can fall into a legal and ethical gray area.
- Cybersecurity Researchers: Professionals who study software and systems to discover vulnerabilities. Their role is crucial in the proactive defense against potential Zero Day Attacks by identifying and disclosing vulnerabilities responsibly.
- Attackers (Black Hat Hackers): Malicious actors who seek to discover and exploit vulnerabilities for personal gain, sabotage, espionage, or other harmful motives.
Finally you should know The Ultimate Guide to Test Data Management Tools.
Examples of Zero Day Attacks
Zero Day Attacks have left a significant mark on the digital landscape, with several high-profile incidents highlighting the potential impact and consequences of these attacks. Here’s an overview of notable Zero Day Attacks across various platforms and the lessons learned from these breaches:
Google Chrome:
One notable attack targeted a vulnerability in the Google Chrome web browser. Attackers exploited a flaw that allowed them to execute malicious code on the user’s system. Google swiftly released a patch, but the incident underscored the importance of keeping web browsers up to date to protect against similar vulnerabilities.
Zoom Video Communications:
During the height of its usage amidst global lockdowns, Zoom faced a Zero Day Attack that exploited vulnerabilities in its software, compromising user security. This led to significant scrutiny of Zoom’s security practices and prompted rapid enhancements to its security protocols.
Apple iOS:
A sophisticated Zero Day Attack targeted iPhone users through vulnerabilities within the iOS operating system. This attack, attributed to nation-state actors, was designed to surveil human rights activists and journalists, highlighting the potential for Zero Day Attacks to breach even highly secure environments.
Microsoft Windows in Eastern Europe:
A series of Zero Day Attacks exploited vulnerabilities in Microsoft Windows, targeting users primarily in Eastern Europe. These attacks were part of a cyber espionage campaign, illustrating the geopolitical dimension of cyber threats.
Microsoft Word:
Attackers exploited a Zero Day Vulnerability in Microsoft Word, allowing them to distribute malware through seemingly innocuous documents. This attack demonstrated the need for caution when opening attachments, even from trusted sources.
Stuxnet:
Perhaps the most famous Zero Day Attack, Stuxnet was a highly sophisticated piece of malware that targeted industrial control systems used in Iran’s nuclear program. Utilizing multiple Zero Day Vulnerabilities, it caused significant damage to Iran’s uranium enrichment facilities. Stuxnet is a prime example of a nation-state leveraging Zero Day Attacks for geopolitical aims.
The impact of these attacks ranges from individual data breaches to global political consequences, underscoring the critical importance of cybersecurity vigilance.
How to Detect Zero Day Attacks?
Here are key aspects of detecting Zero Day Attacks and the roles of emerging technologies in this domain:
- Behavior Analysis and Heuristics: Traditional signature-based detection methods are ineffective against Zero Day Attacks because they rely on known patterns. Instead, behavior analysis and heuristic-based detection focus on identifying suspicious behavior or anomalies in system operations, which can indicate a Zero Day Exploit in action.
- Machine Learning and AI: These technologies can analyze vast amounts of data to identify patterns and behaviors that deviate from the norm, learning over time to better recognize potential threats. Machine learning algorithms can adapt to new and evolving attack strategies, potentially identifying Zero Day Exploits by their effects on the system or network security before specific signatures have been developed.
- Threat Intelligence Sharing: Collaborating and sharing threat intelligence among organizations, cybersecurity vendors, and governmental agencies can help in the early detection of Zero Day Attacks. When information about new vulnerabilities or emerging threats is shared in real-time, it can significantly improve the collective ability to detect and respond to Zero Day Attacks more effectively.
- Sandboxing: Sandboxing involves executing suspicious code or software in a controlled environment separate from the main network or system. This allows security teams to observe the behavior of the code without risking the main system’s integrity, potentially identifying malicious actions indicative of a Zero Day Exploit.
- Endpoint Detection and Response (EDR): EDR solutions provide comprehensive monitoring and response capabilities at the endpoint level. By analyzing events and behaviors on endpoints, EDR tools can identify indicators of a Zero Day Attack, even in the absence of known malware signatures.
Have an eye on the Evolution of Virtual Datarooms– From Simple File Sharing to Secure Collaboration.
How to Protect Your Entity from Zero Day Attacks?
Defending against Zero Day Attacks requires a multifaceted approach, combining technology, processes, and people. Given the inherent unpredictability of these attacks, the focus should be on layered security measures and rapid response capabilities. Here are best practices for individuals and organizations aiming to safeguard against Zero Day Threats:
- Regular Software Updates: Keeping all software and systems up to date is fundamental. Developers often release patches for vulnerabilities as soon as they’re discovered. Regular updates ensure these patches are applied, closing potential entry points for attackers.
- Use of Advanced Security Solutions: Antivirus and antimalware solutions, especially those equipped with heuristic and behavior-based detection capabilities, can help identify and block suspicious activities that may indicate a Zero Day Exploit.
- Implementing Security Best Practices: Adopting a robust security framework, including the use of firewalls, intrusion detection systems, and secure coding practices, forms a critical line of defense.
- Employment of Threat Intelligence: Leveraging threat intelligence services can provide early warnings about new vulnerabilities and emerging threats, allowing organizations to proactively adjust their security posture.
- Ethical Hacking and Regular Security Assessments: Engaging in ethical hacking and conducting regular security assessments can uncover potential vulnerabilities before they can be exploited by attackers. Penetration testing, in particular, is valuable for testing an organization’s defenses.
- Security Awareness Training: Educate employees about the importance of cybersecurity, recognizing phishing attempts, and safe browsing practices. It can significantly reduce the risk of successful attacks.
- Zero Trust Architecture: Implementing a Zero Trust security model, where no entity is trusted by default from inside or outside the network. It can minimize the potential impact of a breach.
- Data Encryption: Encrypting sensitive data or data security in an organization, both at rest and in transit, can protect the integrity and confidentiality of information, even in the event of a system compromise.
- Regular Backups: Maintaining regular backups of critical data in secure, separate locations ensures that, in the event of an attack, organizations can recover their data with minimal loss.
Final Words
Zero-Day Attacks is one of the many cybersecurity trends of 2025. Demystifying Zero-Day Attacks requires a multifaceted approach that combines technological defenses, user education, and industry collaboration. While the unseen threats may continue to evolve, a proactive and informed cybersecurity strategy is paramount in safeguarding against the potential consequences of Zero-Day Attacks. Stay vigilant, stay informed, and together we can build a more resilient digital future.








Leave a Reply